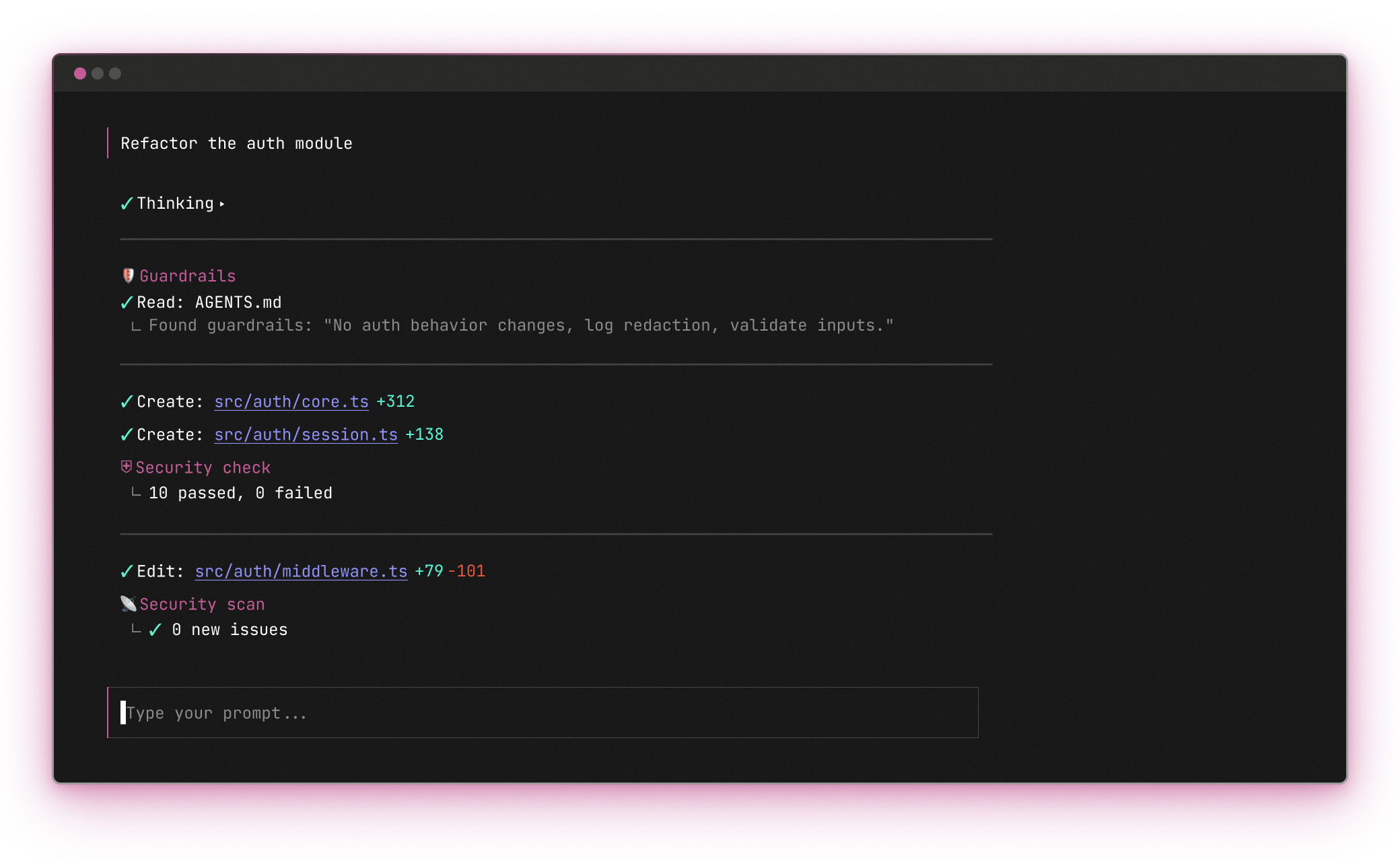
Your AI copilot is quietly taking things away
Every insecure or non-compliant line of AI-generated code costs you something. Academic research shows nearly half of AI-written code introduces risk by expanding your attack surface, undoing developer work, and draining the productivity gains AI was supposed to deliver.